Suspected Iranian hackers targeting LinkedIn users to spread malware through fake Dream job offers, according to ClearSky Cyber Security.
According to security researchers, Iranian hackers are posing as fake recruiters on LinkedIn and sending “Dream job” offers to LinkedIn users. With enticing job offers they intended to trick them into running Windows-based malware, as these job offers are nothing but a ZIP file containing a malicious executable program, according to Israeli company ClearSky Cyber Security.
What is Iranian hackers Dream job offers?
- “Dream job” offers are posted on LinkedIn by Iranian hackers to target LinkedIn users and trick them into downloading a ZIP file containing a malicious executable program.
- It has been said by cybersecurity vendor that “The campaign distributed the SnailResin malware, which activates the SlugResin backdoor”. If users install these malware, then it can be used as secret spy on affected computer to steal passwords and load other malware.
- The Iranian hackers send an email as a part of fake job recruiters including attached job-related documents. The ZIP file send by them contain a mix of legitimate and malicious files to make the job offer look credible.
- Since September 2023, this “Dream job” campaign has been active. The main goal of this campaign was phishing people those who work in the aerospace, aviation, and defense industries, particularly in Israel and Eastern Europe.
- The aim of Iranian hackers is to acquire sensitive information and potentially disrupting operations within these critical sectors, as said by the ClearSky in its reports.
- It has been found by ClearSky Cyber Security that Iranian hackers Dream job campaign has links to a notorious North Korean hacking group called “Lazarus”. Iranian hackers adopted the malware tools from Lazarus, to impersonate the North Korean group and disguise the origin of the attacks.
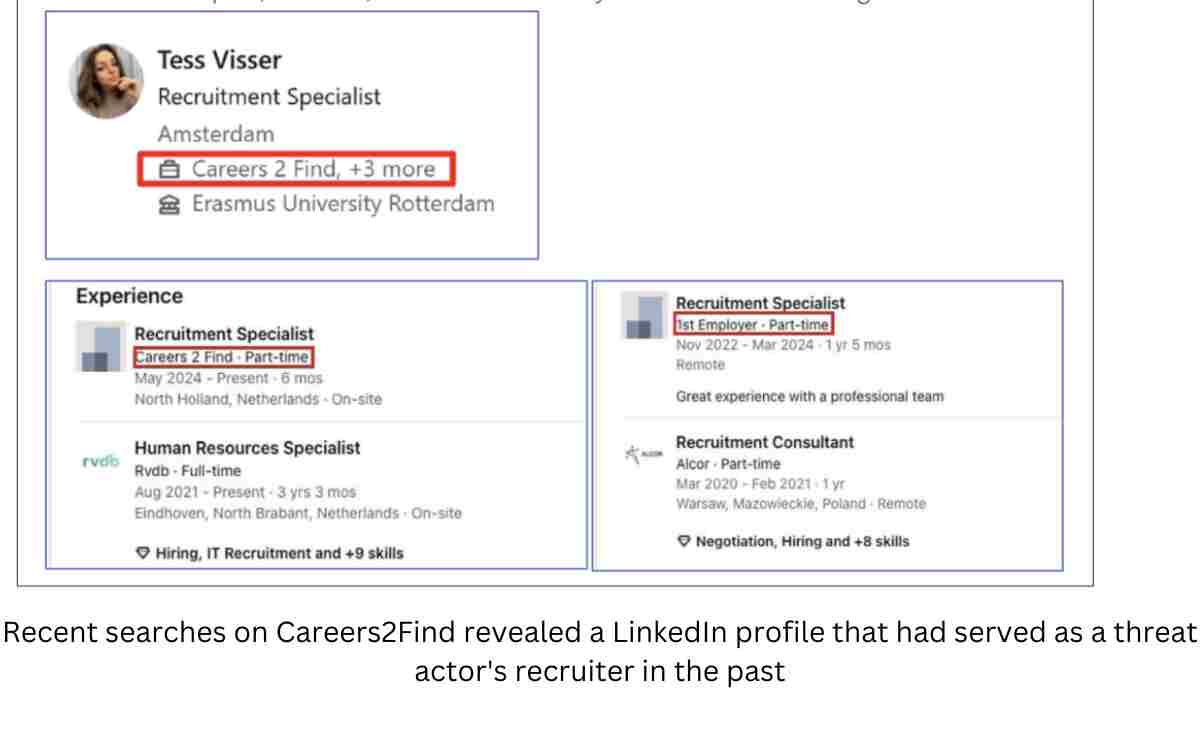
One more fake job recruiting website has been created by the Iranian hackers called “Career 2 Find”. In this fake job website, a detailed PDF guide has been given to Victims on how to ‘safely’ access the website but actually, the PDF contains steps to ensure the victim correctly executes the malware, said by ClearSky.
Well, the hacking campaign to the Iranian hacking group Charming Kitten, citing IP addresses used in the attacks has been traced by the Israeli company. Specifically, the fake careers2find[.]com site led to a domain that’s been connected to previous hacking campaigns from Charming Kitten.
For more such latest updates, stay tuned with Technology Navigator, your daily dose of technology.
